Reflection of Hack on Fractured Online
Greetings, all! I’m excited to share a post that delves into the aftermath of a recent security incident involving the game Fractured Online.
Greetings, all! I’m excited to share a post that delves into the aftermath of a recent security incident involving the game Fractured Online.
You can find details about the attack here: Fractured Attack Breakdown
It’s important to note that the primary focus of this post isn’t to dissect the specifics of the hack (as they are still unclear at the time of writing). Instead, the goal is to provide thoughtful reflections on various security-related topics arising from this incident.
Risk management
This kind of attacks underscores the critical importance of robust risk management strategies. As we delve into the incident, one pivotal aspect emerges: the testing and evaluation of internal APIs. Often, internal APIs are not subjected to the same rigorous testing protocols as their client-side counterparts, leaving potential vulnerabilities unnoticed.
A foundational step in understanding and mitigating risks is a thorough examination of the attack surface. In this instance, there might have been a misconception among developers that the API in question was strictly internal, leading to a potential oversight in assessing its security posture. The assumption that no external entity should have access to the API may have inadvertently contributed to a false sense of security.
Considering the threat landscape, internal attackers pose a unique challenge. In scenarios where an API is perceived as internal and not adequately protected, a malicious insider could exploit their privileged position. This raises crucial questions about assessing internal user privileges and potential actions they could undertake.
To measure and manage such risks within a company, a comprehensive approach is essential. Conducting regular audits and vulnerability assessments on internal APIs, even those deemed internal, is paramount. A robust access control mechanism should be in place, ensuring that only authorized personnel can interact with sensitive APIs. Continuous monitoring and logging of API activities contribute to real-time threat detection, enabling swift response to any suspicious behavior.
Internal user privileges should be meticulously defined, adhering to the principle of least privilege. Regularly reviewing and updating these privileges based on job roles and responsibilities is vital to prevent unauthorized access or misuse. Implementing a robust identity and access management (IAM) system helps enforce these principles and ensures that internal users only have access to the resources necessary for their tasks.
Production changes
In the contemporary landscape characterized by the prevalence of Infrastructure as Code (IaC) and Continuous Integration/Continuous Deployment (CI/CD) practices, the conventional wisdom increasingly discourages the execution of manual tasks within production environments. Presently, numerous organizations unequivocally recognize this principle in the context of infrastructure, servers, and Docker images. However, a recurring pattern persists in the modification of production environments, often involving:
Despite the advancements in automated deployment and configuration management, certain operational practices continue to rely on manual interventions, particularly in scenarios involving database interactions and administrative APIs utilization within production environments.
Making direct changes to a production database through APIs with admin privileges poses significant security and integrity risks. To circumvent these challenges, organizations can implement a series of safeguards and alternative methodologies. A fundamental strategy is to adopt a microservices architecture with well-defined APIs that adhere to the principle of least privilege. Instead of exposing broad admin capabilities, APIs should be granular, allowing for specific actions tied to necessary business functions.
A viable alternative is to introduce an event-driven architecture, where changes are triggered by specific events, and subsequent actions are automated. This ensures that modifications to the database are initiated in response to predefined events, such as user actions, without the need for direct API calls. This event-driven approach provides a more controlled and auditable method for managing data changes, reducing the risk of accidental or malicious alterations.
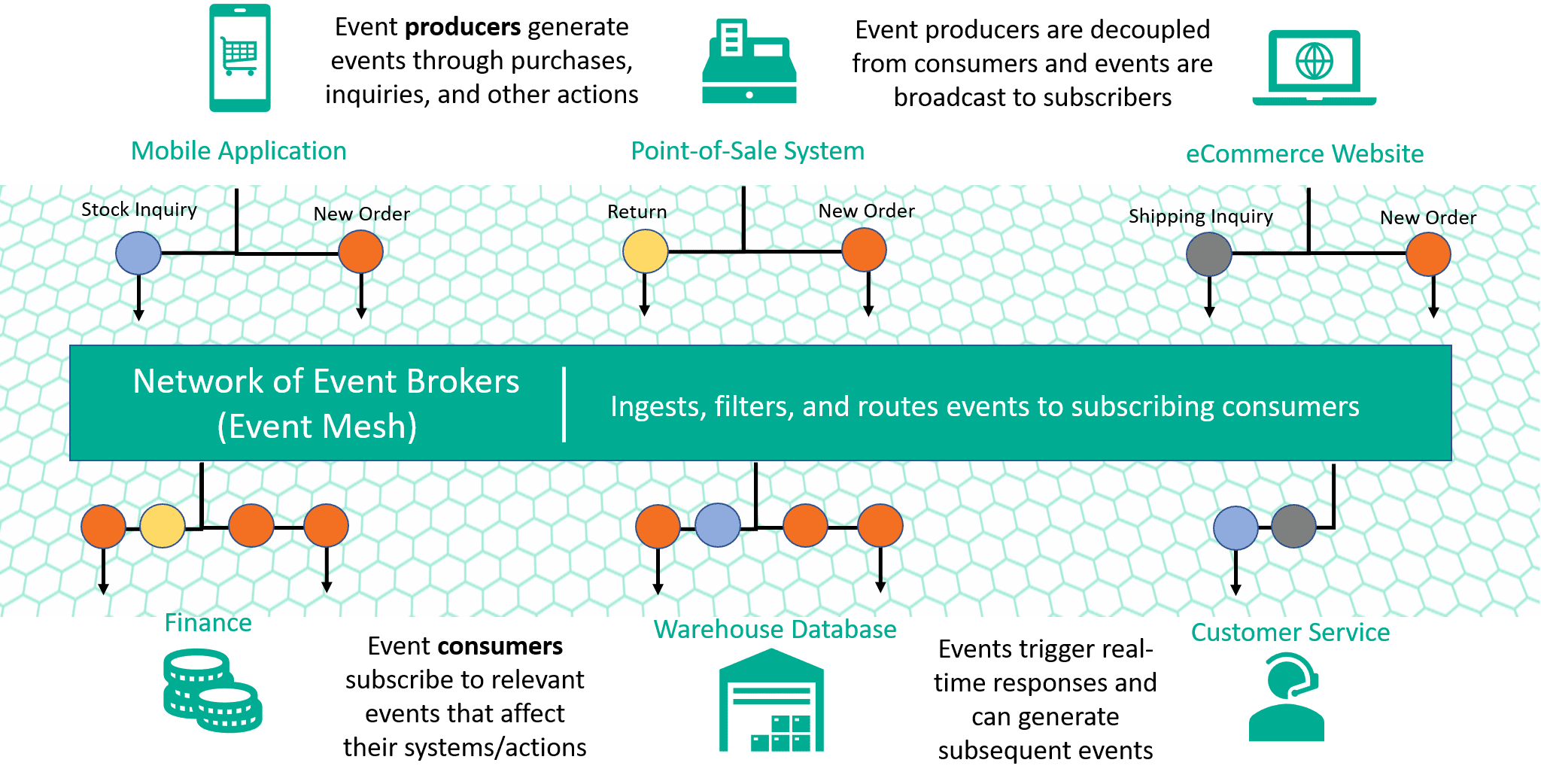
In the case of the vulnerable functionality developers should change the logic related to the deletion of the cities. In which scenarios should a city be deleted?
In those cases developers could create a simple Pub/Sub architecture where the API that deletes cities would get the event and execute the change. This architecture would avoid the need to have a dangerous and powerful API.
If, despite best efforts, there’s a necessity for direct database changes via APIs, stringent mitigations are imperative. Some of the following alternatives could be used:
Furthermore, consider implementing a dual-control principle, requiring multiple authorizations for critical actions. This adds an additional layer of security, preventing a single compromised account from making unauthorized changes. Regularly review and update API security protocols, staying abreast of evolving threats and vulnerabilities.
Impact of a hack in video game industry
The aftermath of a security breach within the gaming community extends far beyond the technical implications; it permeates the very essence of the player experience. The sensitivity and fidelity of players, crucial elements in the gaming ecosystem, come sharply into focus when faced with an incident like the recent hack that resulted in the deletion of player data. As players often invest not just time but emotions into their virtual worlds, the repercussions of such events can be profound.
Individual voices within the gaming community echo the broader impact of such breaches. A player lamented,
This sucks. I’ve bought this a couple of days ago and I was really enjoying it. Hope they can sort it.
The emotional investment in a game can be substantial, and disruptions caused by hacks can abruptly sever the enjoyment and engagement that players derive from their virtual adventures.
Another player, on the verge of joining the community, expressed their disappointment,
Ugh, I was literally about to buy this today.
This sentiment encapsulates the delicate balance that game developers must maintain—a delicate balance between attracting new players and retaining the loyalty of existing ones. Security breaches not only jeopardize the trust of current players but also cast a shadow on potential newcomers’ decision-making.
Conclusion
In the dynamic realm of software development, safeguarding every line of code against the ever-evolving landscape of cyber threats poses an immense challenge. The swift pace of development and the perpetual demand for innovation often place companies in a delicate balancing act, juggling between pushing boundaries and fortifying defenses. It is an era where limited resources can become a bottleneck in the race to secure digital ecosystems.
As evidenced by recent incidents, the gaming industry serves as a poignant example of the vulnerabilities inherent in software, despite the best efforts of talented development teams. Player experiences, often intricately woven into the fabric of these digital realms, can be disrupted in an instant by a security breach.
Recognizing the complexities and constraints faced by companies, our mission is clear—to stand alongside development teams and offer support in the battle against potential hacks. We understand that the commitment to security goes beyond lines of code; it is about fostering a culture of vigilance and resilience. Our company is here to provide the expertise and resources needed to bolster cybersecurity measures, ensuring that the immersive worlds created by developers remain secure, and player trust is unwavering.
In a landscape where the digital frontier expands at breakneck speed, we extend our hand to guide companies through the intricacies of securing their software. As technology evolves, so too does the threat landscape, and by joining forces, we can navigate these challenges together, fortifying the foundations of the digital experiences that captivate and inspire users worldwide.