VulturSec Mobile Methodology
Mobile penetration testing is different than traditional penetration testing, just like mobile applications are different than traditional ones.

Mobile penetration testing is different than traditional penetration testing, just like mobile applications are different than traditional ones. The Mobile environment offer many features/possibilites to build complex and powerful functionalities, but it adds unique attack surface that developers aren’t awere of. The gap between web applications and mobile applications, and the lack of specific knowledge on the OS where application is running leads to critical vulnerabilities that affect your clients and the image of your company.
The following image shows a typical mobile application architecture with resources created and used by the application and the attack surface in the given environment:
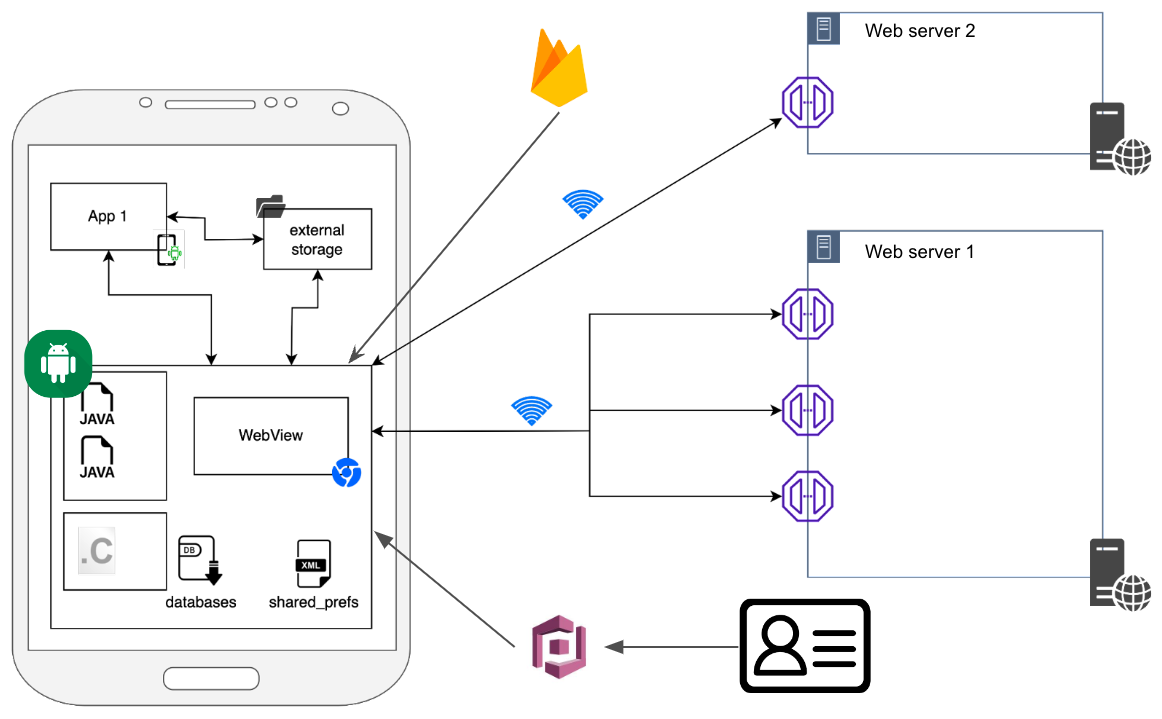
Mobile environments can be compromised in a variety of ways and misconfigurations that can leave your application to external attackers (mostly rogue applications that are being installed in a client cellphone). Also the developer needs to be aware of the different versions of the OS where the applications is going to be installed because new functionalities or changes on default versions can generate new attack vectors the application is not built to avoid.
VulturSec specialists know the complexity of being up to date with security trends and changes in the different versions of the most important mobile operating systems, and the multiple attack vectors each environment has. The security assessment of a Mobile application generally has two analysis steps: static and dynamic.
The static analysis step is executed in order to understand the inner behavior of the application and generally leads to the identification of complex attack vectors that might not be easy to detect dynamically. Also in this step the Vultursec assessment team analyses the configuration on the different components that the application has in order to provide the best recommendations to keep the application UX as it is and adding a layer of security.
In this step VulturSec team executes mainly the following tasks:
The dynamic analysis step is executed in order to understand the information being manipulated on the application, the way the application communicates with the server and how it stores the information in the phone.
In this step VulturSec team executes mainly the following tasks:
We provides you with a report at the end of the process that details all vulnerabilities and opportunities of improvement discovered, as well as attack narratives for any complex attack paths taken. We provide up-to-date and contextual risk ratings for each finding, along with guidance to perform effective remediation.
Our reports aim to help you understand the weaknesses within your environment, what risks those weaknesses bring and we aid you with the remediation process.