VulturSec SDLC Methodology
A long time ago security was a desired aspect on any application, sometimes it was seen as an optional feature as it was thought that it didn’t add any value to the product.

A long time ago security was a desired aspect on any application, sometimes it was seen as an optional feature as it was thought that it didn’t add any value to the product. That was why the security team was never involved on the development of the application, or it was involved when the application was ready to be deployed in the production environment. Luckily the software engineering industry matured and evolved. Nowadays in most industries security is a must, or even there are laws that makes the companies accountable of any security issue.
Security applies at every phase of the software development life cycle (SDLC) and needs to be at the forefront of your developers’ minds as they implement your software’s requirements. With dedicated effort, security issues can be addressed in the SDLC pipeline well before deployment to production. This reduces the risk of finding security vulnerabilities in your app and works to minimize the impact when they are found.
The only problem most companies face regarding this new security paradigm is that they need someone with development knowledge, experience in the SDLC and also that knows about security, the way hackers attack companies and how to reduce the attack surface. VulturSec is here to close the gap between development and security by tackling several activities to convert the SDLC into a Secure Software Development Lifecycle
Secure SDLC’s aim is not to completely eliminate traditional security checks, such as penetration tests, but rather to include security in the scope of developer responsibilities and empower them to build secure applications from the outset.
In the following schema you can find what kind of exercises we execute in each step of the SDLC:
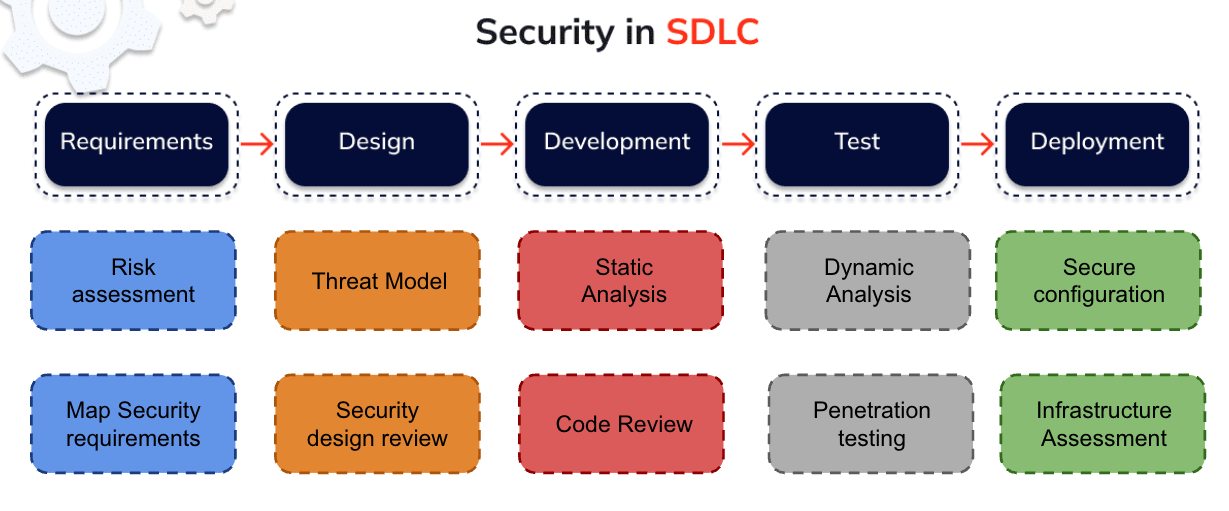
During the requirements phase we propose the following activities:
Risk assessment: In this activity we try to identify and understand the risk factors that have the potential to cause harm to the application. In this exercise we go into different aspects of the company and the environment where the application will be deployed. We also identify alternatives to eliminate or mitigate the risk.
Map security requirements: In this activity we gather with the functional analysts, PO and stakeholders in order to identify non functional requirements related to core security aspects (confidentiality, integrity, availability).
During the design phase we propose the following activities:
Threat Model: In this activity we work to identify, communicate, and understand threats and mitigations within the context of protecting the core assets that the application will manage. A threat model is a structured representation of all the information that affects the security of an application. In essence, it is a view of the application and its environment through the lens of security.
Security Design Review: In this activity we review the design of the application, the protocols used for authentication/authorization and the persistence layer in order to detect flaws in the design or aid in the design of security features.
During the development phase we propose the following activities:
Static Analysis: When it’s time to actually implement the design and make it a reality, concerns usually shift to making sure the code well-written from the security perspective. There are usually established secure coding guidelines as well as code reviews that double-check that these guidelines have been followed correctly. VulturSec team helps in the configuration and implementation of a Source Code Analysis tool.
Code Review: In this activity the assessment team executes a thorough code review of a specific amount of functionalities to deploy. This activity is ideal for iterative developments after the assessment team executed multiple reviews on the whole application.
During the test phase we propose the following activities:
Dynamic Analysis: The assessment team can aid in the process of Dynamic Analysis tools implementation and configuration. The idea of this step is to automate the scan of the application in the CI/CD pipeline to detect dynamic vulnerabilities.
Penetration Testing: Execution of a classic penetration test of the application. This exercise is ideal on the first iterations of the assessment in order to find critical vulnerabilities before the application is launched on production.
During the deployment phase we propose the following activities:
Secure Configuration: In this activity the assessment team validates the configuration of the environment where the application is going to be deployed. Even when the application does not have vulnerabilities, an attacker could abuse the environment where the application is running to get priviliged access or loose security configurations.
Infrastructure Assessment: In this activity the assessment team validates the infrastructure used for the application. We review the cloud services used, the kubernetes and docker configurations in order to find improvements on the services and components used.
The idea in this service is to aid the development process in each phase and complement the security team of your company. So you will decide where you want our services to be used based on the security demands of the moment or based on the skills of the team you have. The VulturSec specialists will integrate the security and development team on your company, work in the way the company works and use the tools the company uses. AppSec Engineer as a Service is our offer.